Xiaomi Redmi Note 7 (xiaomi-lavender)
 Redmi Note 7 | |
| Manufacturer | Xiaomi |
|---|---|
| Name | Redmi Note 7 |
| Codename | xiaomi-lavender |
| Released | 2019 |
| Type | handset |
| Hardware | |
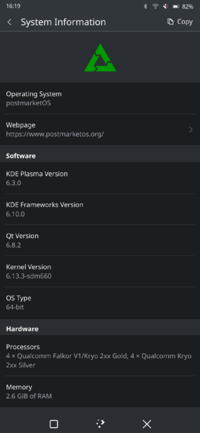
| Chipset | Qualcomm Snapdragon 660 (SDM660) |
| CPU | 8-core (4x 2.2 GHz Kryo 260 & 4x 1.8 GHz Kryo 260) |
| GPU | Adreno 512 |
| Display | 1080 x 2340 |
| Storage | 32/64/128 GB |
| Memory | 3/4/6 GB |
| Architecture | aarch64 |
| Software | |
| Original software | Android (MIUI) |
| Original version | 9 (MIUI 10) |
| FOSS bootloader | partial |
| postmarketOS | |
| Category | testing |
| Pre-built images | no |
| Mainline | yes |
| postmarketOS kernel | 6.13 |
| Flashing |
Works |
|---|---|
| USB Networking |
Works |
| Internal storage |
Works |
| SD card |
Works |
| Battery |
Works |
| Screen |
Works |
| Touchscreen |
Works |
| Multimedia | |
| 3D Acceleration |
Works |
| Audio |
Broken |
| Camera |
Broken |
| Camera Flash |
Broken |
| Connectivity | |
| WiFi |
Partial |
| Bluetooth |
Works |
| GPS |
Broken |
| Modem | |
| Calls |
Broken |
| SMS |
Broken |
| Mobile data |
Broken |
| Miscellaneous | |
| FDE |
Works |
| USB OTG |
Broken |
| Sensors | |
| Accelerometer |
Works |
| Magnetometer |
Broken |
| Ambient Light |
Broken |
| Proximity |
Broken |
| Haptics |
Works |
| Primary Bootloader |
Broken |
|---|---|
| Secondary Bootloader |
Partial |
| Internal Storage |
Works |
| SD card |
Broken |
| USB Host |
Broken |
| USB Peripheral |
Works |
| Display |
Works |
| Keyboard |
Broken |
| Buttons |
Partial |
| This device is based on the Snapdragon 660. See the SoC page for common tips, guides and troubleshooting steps |
Contributors
Maintainer(s)
Users owning this device
- Alexeymin (Notes: Test subject #1)
- Alikates
- Bczeman
- Danct12
- Fann (Notes: 4/64 LineageOS daily driver)
- Hitechshell
- Jcgruenhage (Notes: Temporarily on LineageOS)
- Kalwardin (Notes: Main device, Lineage OS)
- NekoCWD (Notes: 6/64GB LineageOS second phone)
- Perigoso
- Sprite Night (Notes: 4/64 daily driver, bloated battery)
- Vimsky (Notes: Main device, UBports)
Device variants
There are at least 3 variants of lavender with different combintaions of panel and touchscreen:
- BOE panel + some touchscreen unknown to science "synaptics-tcm" (only panel is suuported, no ts driver ported yet)
- Shenchao panel + Novatek touchscreen (not supported at all yet, but tianma variant may work on pmos kernels 6.10, 6.11)
- Tianma panel + Novatek NT36672A touchscreen (fully supported)
In order to identify your device variant, easiest way is to look at /proc/cmdline while running Android (in Android you need root for this, in TWRP you need nothing). Look for part starting with mdss_mdp.panel=. For example you see this:
mdss_mdp.panel=1:dsi:0:qcom,mdss_dsi_nt36672a_shenchao_fhdplus_video:config0:1:none:cfg:single_dsi
This means that you have shenchao panel.
How to enter flash mode
Bootloader Unlocking
Like other Xiaomi devices, the user will have to acquire the bootloader unlock key: https://en.miui.com/unlock
The device will not unlock if the device isn't 7 days old (from the time when your device connects to internet and powered on, and linked with Mi Account)
Recovery mode
- Turn the device off (or restart also works)
- Hold and button
- Once you feel vibration and phone turns on, release button
- Keep holding until you get to recovery.
Flashing (Download, Fastboot) mode
- Same as recovery, but this time hold the and keys.
Fastboot boot
In theory pmbootstrap flasher boot allows to directly boot kernel through USB without flashing it, but does not currently work. Bootloader does not like something about kernel compression:
Bootloader UART logs during "pmbootstrap flasher boot":
But it was reported to work for some people. Try it, might work for you
Installation
- Install pmbootstrap first on your PC
- make sure you have TWRP installed on the phone, it will help you to make backups:
- backup
boot,dtboandsystempartitions first from TWRP, something like this, for example, to SD card:
adb shell dd if=/dev/block/bootdevice/by-name/boot of=/external_sd/backups/orig_boot.img dd if=/dev/block/bootdevice/by-name/dtbo of=/external_sd/backups/orig_dtbo.img dd if=/dev/block/bootdevice/by-name/system of=/external_sd/backups/orig_system.img
- in ADB shell (or in TWRP Advanced -> Terminal) execute
cat /proc/cmdlineand see which panel type is mentioned there - zap & reinit pmbootstrap (
pmbootstrap -y zap ; pmbootstrap init), choose vendorxiaomiand devicelavender - choose your panel variant correctly (BOE or Tianma)
- proceed with installation as usual: reboot device to fastboot mode, then:
pmbootstrap install pmbootstrap flasher flash_kernel pmbootstrap flasher flash_rootfs pmbootstrap flasher flash_vbmeta fastboot erase dtbo
And finally
fastboot reboot
WI-Fi
Marked as partial, because there is modem crash on attempt to disconnect from Wi-Fi, looks like this in dmesg:
[ 4383.715292] wlan0: failed to remove key (0, redacted) from hardware (-110) [ 4383.968264] qcom-q6v5-mss 4080000.remoteproc: fatal error received: err_qdi.c:459:EX:wlan_process:1:WLAN RT:2083:PC=b00c87e0 [ 4383.968304] remoteproc remoteproc1: crash detected in 4080000.remoteproc: type fatal error
After that ath10k driver fails to handle remoteproc crash very well and you can't make it probe fine again, even re-inserting module doesn't help. Only reboot. But if you don't disconnect from Wi-Fi, it works fine.
Photos
-
Weston on downstream kernel
-
Lavender booting mainline
-
PlaMo on fbdev 1
-
PlaMo on fbdev 2
-
X11 (Xfce) on fbdev
-
Plasma Desktop on fbdev
-
lavender running Plasma Mobile #1
-
lavender running Plasma Mobile #2
Additional info
Partition list
Partition list
Android Verified Boot (vbmeta)
This device is using Android_Verified_Boot_(AVB) so, if you did not flash any custom Android ROM, you may need to flash vbmeta partition with vbmeta.img with verification disabled flag. pmbootstrap now can generate such empty vbmeta image and flash it with one command:
$ pmbootstrap flasher flash_vbmeta
DTBO partition
This device is using a dedicated partition to store the Device Tree Blob Overlay. Read more at https://source.android.com/devices/architecture/dto/partitions .
Update: looks like dtbo partition is not used during boot by LineageOS's kernel, because it is using appended DTB (CONFIG_BUILD_ARM64_APPENDED_DTB_IMAGE=y)
Update2: device tree from dtbo partition is used by bootloader to apply some fixups on top of appended dtb. Bootloader tries to apply overlay dtb from dtbo partition over a dtb found appended to kernel, and if it fails to do so, it falls back into fastboot mode. Example bootloader debug UART output in that case:
Memory Base Address: 0x40000000 Decompressing kernel image start: 2700 ms Decompressing kernel image done: 2852 ms ufdt apply overlay failed Launching fastboot
See also Zhuowei's notes on creating custom dtbo partition: https://gitlab.com/zhuowei/dtbo-google-crosshatch-mainline
For mainline kernel just fastboot erase dtbo works. Bootloader ignores missing dtbo, example output when dtbo partition is erased:
Memory Base Address: 0x40000000 Decompressing kernel image start: 2641 ms Decompressing kernel image done: 2793 ms Dtbo hdr magic mismatch 0, with D7B7AB1E Best match DTB tags 317/00020008/0x00000000/0/1001B/102001A/0/0/(offset)0x97128304/(size)0x00000653 Using pmic info 0x1001B/0x102001A/0x0/0x0 for device 0x2001B/0x102001A/0x0/0x0 Memory Base Address: 0x40000000 smem protocol = 9C2FA0A0 board_id1 is 1 board_id2 is 1 board_id3 is 0 board_id is 1 get_boardid_from_smem,SUCCESS ,board_id=0x102,cpu_id=0x39148C8C,hwdefined=0 PON Reason is 17 cold_boot:1 charger path: 1 ...(proceeding to normal boot procedure)...
For downstream kernel, leave stock dtbo partition untouched.
Bootloader cmdline
Stock bootloader is doing nasty things with kernel command line: it passes a lot of arguments that make booting custom OS (like postmarketOS) impossible
Full list of stock command line parameters:
ramoops_memreserve=4M comes from defconfig, next from boot.img, others (starting with first androidboot. and below) come from bootloader directly.
Harmful kernel command line params from bootloader
Options like root=, skip_initramfs make kernel look for a specific partition to mount at /, skipping initramfs, which is incompatible with default booting methods of postmarketOS. That's why some tricky patches are needed like by opendata26: init: ignore bootloader cmdline params for mounts
Some info on skip_initramfs kernel cmdline parameter: https://forum.xda-developers.com/apps/magisk/pixel-2-pixel-2-xl-support-t3697427/post74361728#post74361728
Since version 6.9 postmarketOS's close-to-mainline linux kernel fork for 630/660 devices contains a workaround to ignore such cmdline parameters - https://github.com/sdm660-mainline/linux/commit/d0b6901c00ceaaad48447cd299545d4872d11b76 .
Way to get boot log
This device known to ship with the oem getlog fastboot command.
This is not a trivial command to use, but it is extremely useful as it allows side-stepping the need to boot in a known working system to use the ramoops console. The output of the command is a jumble, but is still usable for figuring out early boot issues. It is much better than having to rely on a booted system to get the information, but still not as good as having a dedicated serial access.
Example usage follows.
$ fastboot oem getlog 2>&1 (bootloader) [ 0.000000] Booting Linux on physical CPU 0x0 [ 0.000 (bootloader) 000] Initializing cgroup subsys cpuset [ 0.000000] Initi (bootloader) alizing cgroup subsys cpu [ 0.000000] Initializing cgrou (bootloader) p subsys cpuacct [ 0.000000] Initializing cgroup subsys (bootloader) schedtune [ 0.000000] Linux version 4.4.153 (nixbld@loca (bootloader) lhost) (gcc version 4.9.4 (GCC) ) #2 SMP PREEMPT Sat Nov 23 (bootloader) 20:31:33 UTC 2019 [ 0.000000] Boot CPU: AArch64 Process (bootloader) or [51af8014] [...]
As the output of the command is on stderr, here's how to output to a file.
$ fastboot oem getlog > log.txt 2>&1
It is unknown if there are ways to make the output better. (Apply some kind error correction algorithm?)
EDIT: seems to not work for me, whatever you do, the output is:
$ fastboot oem getlog
(bootloader) [Macle]Maybe no last kmsg
OKAY [ 0.000s]
Finished. Total time: 0.000s
Probably needs a crash? But I can read pstore-console (dmesg) logs from booted TWRP recovery fine..


Getting logs through debug UART
You have to disassemble the phone (just removing back cover is enough). You'll have to heat up edges of the back cover (as shown in disassembling video, see Links below) before trying to remove it. Be careful! It is made of glass! Also be careful about fingerprint sensor connector, it is connected to a back cover you are trying to remove. Don't rip it.
In the center you will see 4 test points that are available. (See the picture) Two bigger ones (0.8mm) are EDL (FORCE_USB_BOOT) pins. UART test points are two smaller ones on the left (0.5mm). TP11 is UART TX (gpio 4), TP10 is UART RX (gpio 5). GND is that whole metal shielding, that covers the center of the board. So, to get debug logs from UART it is enough to connect UART TX from the board to RX pin on the converter, and connect GND between phone and GND pin on the converter.
Links
- pmaports!1095 Initial merge request
- Device package
- Mainline kernel package
- Close-to mainline kernel source repository
- Mainline development BLOG
- pmaports#494 (OLD) How to make Wi-Fi work?
- NixOS-mobile lavender MR
- https://www.youtube.com/watch?v=6GqXqW2Nygc Disassembling video (Rus)
- https://www.anandtech.com/show/11338/qualcomm-announces-snapdragon-660-630-mobile-platforms
- List of mobile phones on SDM660 SoC: 1, 2